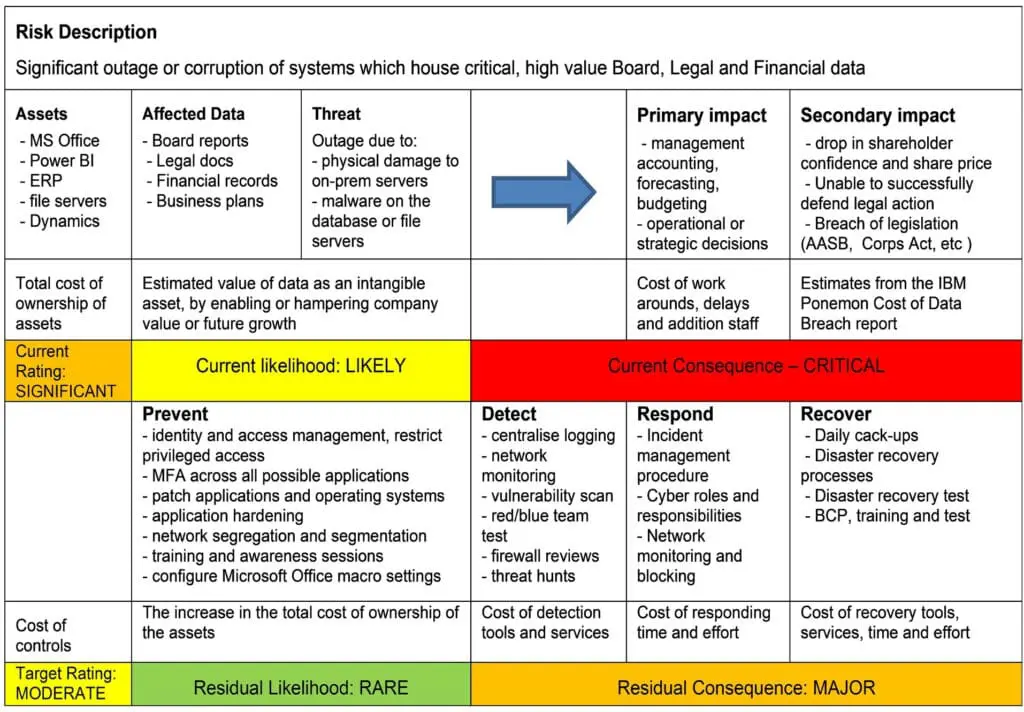
How to measure the dollar value and ROI of cyber security
With the rise of cyber attacks and the myriad of cyber products on the market, it can be difficult to know which cyber security initiatives to focus on to get the best value in terms of spend and effectiveness.