Managed Detection and Response

Proactive protection
Our service uses market-leading tools and industry best practices to examine end-point activity at the process level to search for a wide range of attacker Tactics, Techniques and Procedures (TTPs), alerting Interactive’s A...
Our service uses market-leading tools and industry best practices to examine end-point activity at the process level to search for a wide range of attacker Tactics, Techniques and Procedures (TTPs), alerting Interactive’s Australian-based 24/7 CSOC for triage and response.
Onshore SOC
Peace of mind
End-to-end support
Certified and compliant
Fast, agile

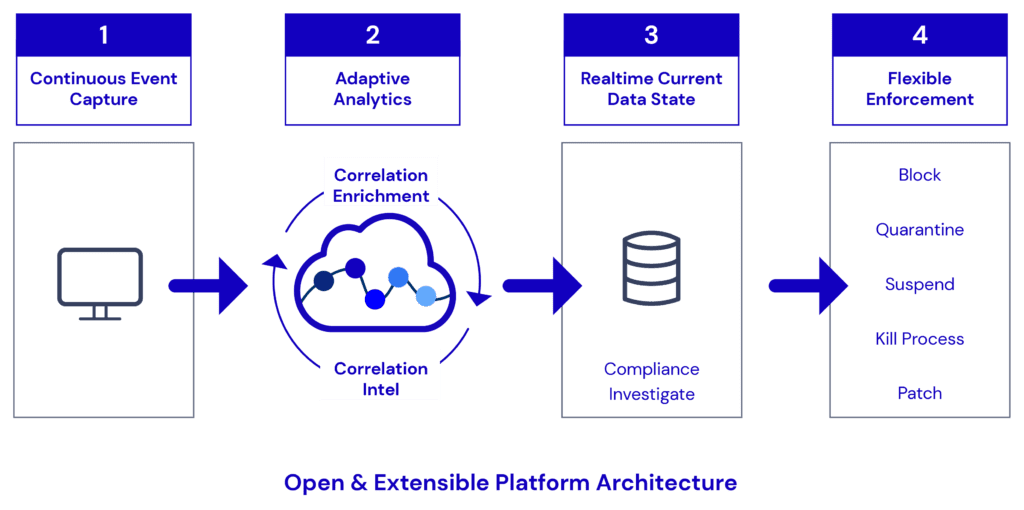
How does Managed Detection Response (MDR) work?
MDR works through installing an agent onto your endpoint assets, which is used to continually monitor your endpoint security events. Our cloud platform analyses the data to either investigate and identify a past security incident or use the data to look for similar threats.
As part of this service, Interactive can perform proactive response measures including the removal of malware, disabling or suspending access, terminating connections or applications and isolating hosts.
You’ll have a choice of two market leading technology options, Microsoft Defender for Endpoint, or Crowdstrike Falcon Enterprise. You can also Bring Your Own Licence (BYOL), or Interactive can arrange licensing on your behalf.
Trusted Australia wide by over 2,000 businesses.



We know our stuff.





Discuss how we can protect your assets and reputation today.
Frequently Asked Questions
FORM HEADINF
- All
- Automotive and Logistics
- Consumer Packaged Goods
- Corporate
- Financial Services
- FMCG
- Government
- Healthcare
- IT, Data and Software
- Manufacturing
- Media and Entertainment
- Philanthropy and Volunteer
- Real Estate
- Retail
- Superannuation
- Travel



